Home » Products & Services » Company Information Security Services » Device Security
Device Security
Comprehensive Cybersecurity for all devices
According to statistics from just one actor, in 2023, researchers recorded 6.06 billion malware attacks worldwide, which was 11% more than the year before.
Reliable security solutions
Nowadays, it is very important that a company's information security is up to date. Protecting data centers and applications may be everyday life for many, but in a mobile remote and hybrid working environment, it is also important to remember to protect endpoints and mobile devices so that the company can operate in a secure IT environment. A large part of information security incidents or attacks occur precisely through the endpoint. The most typical of information security attacks carried out through the endpoint are the phishing scams that have become more common in recent years, in which a fraudulent message disguised as trustworthy gets the user to click on a link, after which the user is redirected to a phishing page that asks for, for example, usernames or personal information.
Modern technology allows cybercriminals to constantly find new and more creative ways to carry out attacks, and for this reason, many companies have moved to implement the “Zero Trust” model, which is the idea that nothing is trusted. The Zero Trust model assumes that the network environment is under constant attack and all data traffic, both outgoing and incoming, is under surveillance. Many companies have made expensive purchases to ensure that the workplace network environment is secure. However, in the remote and hybrid work model, employees' computers are no longer always located in the company's managed and secure network environment, but instead use public wifi networks in employees' homes or public spaces.
Protection regardless of location
In addition to endpoint protection, you need to ensure that the operating system and software versions of the devices are always up to date. Automated IT device management can help with this. JMJepm. In hybrid and remote work with cloud-based With the SASE solution as Cato Networks, which protects users and devices regardless of their physical location.
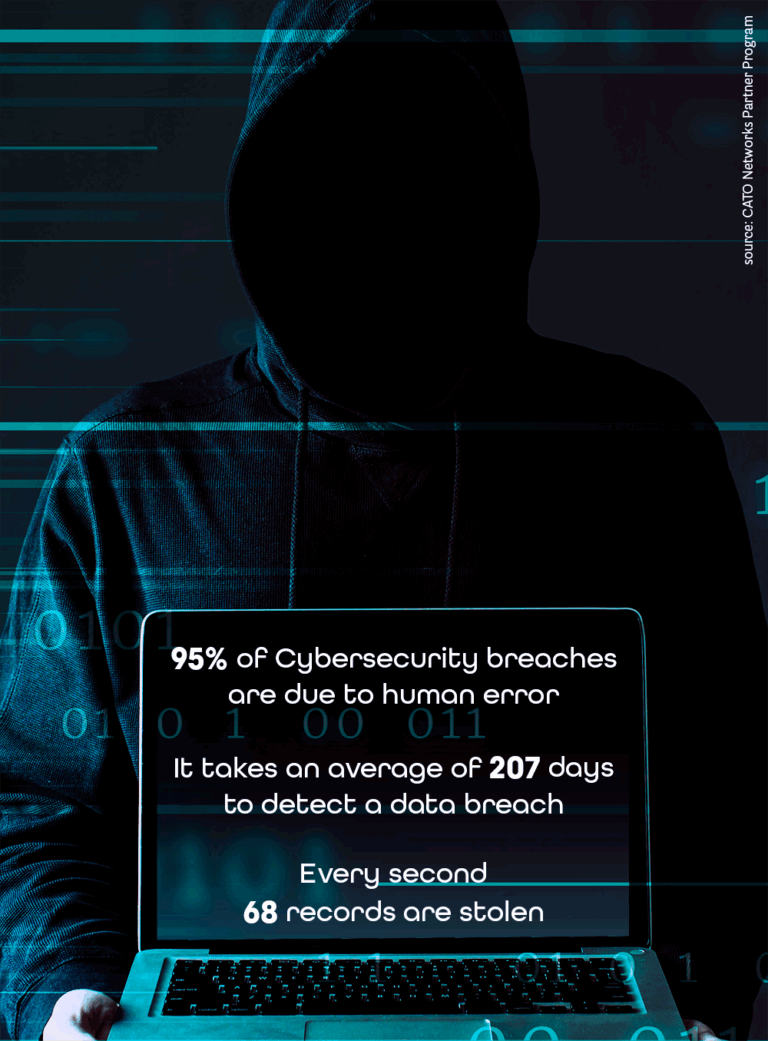
JMJping offers reliable security solutions
to keep your company's data safe,
regardless of where your devices
and employees are located.
Protecting endpoints requires identifying risks
and minimizing the attack surface.
For Computers
WithSecure™ Elements EPP for Computers provides modern and resource-efficient endpoint protection for Windows and Mac computers.
For Servers
WithSecure™ Elements EPP for Servers enables extreme security for Windows, Linux and Citrix server environments.
For Mobile Devices
WithSecure™ Elements Mobile Protection blocks malicious apps and protects against malicious websites. The VPN automatically encrypts all traffic.
WithSecure™ Elements Endpoint Detection & Response
EDR detects anomalies and analyzes entire event chains and their contents.
- Increase visibility
- Detects anomalies
- Analyze event chains
- Enables quick response
for identification and strengthening information security
ransomware attacks in real-time
to prevent new types of cybersecurity threats
resolve most cyber threats automatically
which help monitor the level of protection
and as an additional service for servers


